
Federal authorities and private researchers are alerting companies to a wave of domain hijacking attacks that use relatively novel techniques to compromise targets at an almost unprecedented scale.
The attacks, which security firm FireEye said have been active since January 2017, use three different ways to manipulate the Domain Name System records that allow computers to find a company's computers on the Internet. By replacing the legitimate IP address for a domain such as example.com with a booby-trapped address, attackers can cause example.com to carry out a variety of malicious activities, including harvesting users' login credentials. The techniques detected by FireEye are particularly effective, because they allow attackers to obtain valid TLS certificates that prevent browsers from detecting the hijacking.
“A large number of organizations has been affected by this pattern of DNS record manipulation and fraudulent SSL certificates,” FireEye researchers Muks Hirani, Sarah Jones, Ben Read wrote in a report published Thursday. “They include telecoms and ISP[s], government and sensitive commercial entities.” The campaign, they added, is occurring around the globe at “an almost unprecedented scale, with a high degree of success.”
One DNS hijacking technique involves changing what’s known as the DNS A record. It works when the attackers have somehow previously compromised the login credentials for the administration panel of the target’s DNS provider. The attackers then change the IP address of the targeted domain to one they control. With control over the domain, the attackers then use the automated Let’s Encrypt service to generate a valid TLS certificate for it. Cisco’s Talos team previously described this method.
With that in place, people who visit the targeted domain don’t access its legitimate server. Instead, they access an attacker-controlled server that connects back to the legitimate server to give visitors the impression nothing is amiss. The attackers then collect usernames and passwords. End users receive no warnings and won’t notice any differences in the site they’re accessing except, possibly, for a longer-than-normal delay.
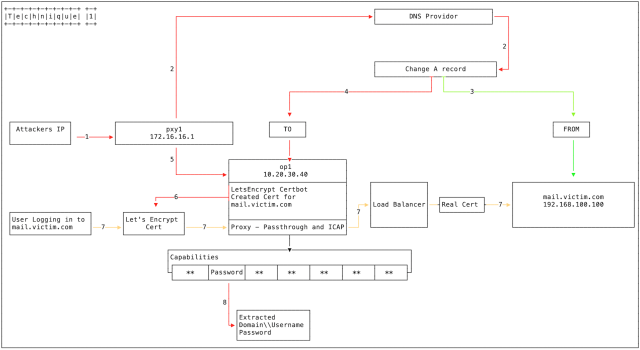
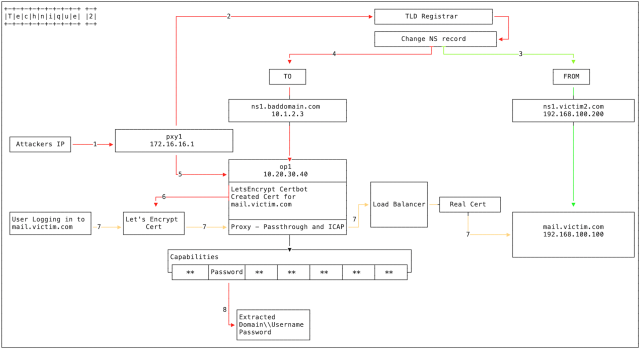
A second technique is similar except that it exploits a previously compromised domain registrar or ccTLD to change name server records.
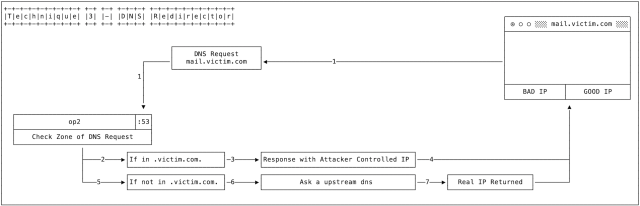
The third technique uses a DNS redirector in tandem with one of the above two methods.
FireEye said attackers are using the techniques to hijack dozens of domains belonging to entities in North America, Europe, the Middle East, and North Africa. The company advised administrators to take a variety of measures, including:
- ensure they’re using multifactor authentication to protect the domain’s administration panel
- check that their A and NS records are valid
- search transparency logs for unauthorized TLS certificates covering their domains and
- conduct internal investigations to assess if networks have been compromised
The researchers assessed with moderate confidence that the attackers had a link to Iran, based on IP addresses they’re using.
“This DNS hijacking, and the scale at which it has been exploited, showcases the continuing evolution in tactics from Iran-based actors,” Thursday’s report concluded. “This is an overview of one set of [tactics, techniques, and procedures] that we recently observed affecting multiple entities. We are highlighting it now so that potential targets can take appropriate defensive action.”
The National Cybersecurity and Communications Integration Center issued a statement that encouraged administrators to read the FireEye report.
reader comments
78