
According to a security researcher for Linux distributer Red Hat, network hardware sold by several manufacturers failed to properly implement a widely used cryptographic standard, a data-leaking shortcoming that can allow adversaries to impersonate HTTPS-protected websites using the faulty equipment.
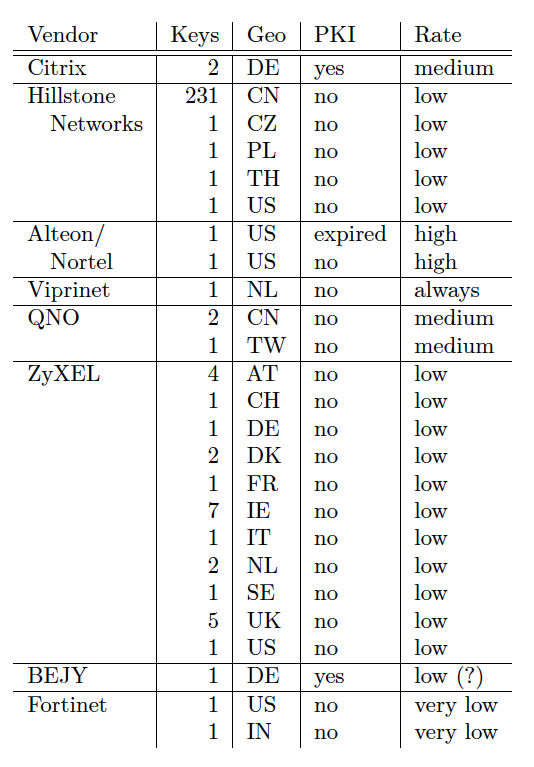
A nine-month scan that queried billions of HTTPS sessions from millions of IP addresses was able to obtain leaked data for 272 keys, reports Red Hat security researcher Florian Weimer in a research paper published this week. Because the scan surveyed only a very small percentage of the overall number of transport layer security protocol handshakes, many more keys and manufacturers are likely to be affected by the leakage. Vulnerable hardware includes load balancers from Citrix as well as devices from Hillstone Networks, Alteon/Nortel, Viprinet, QNO, ZyXEL, BEJY, and Fortinet.
Enter Chinese Remainder Theorem
The leakage is the result of insecure implementations of the RSA public key cryptosystem, which is one of several that HTTPS-protected websites can use to exchange keys with visitors. A 1996 research paper by researcher Arjen Lenstra warned that an optimization based on what's known as the Chinese Remainder Theorem sometimes causes faults to occur during the computation of an RSA signature. The errors cause HTTPS websites that use the perfect forward secrecy protocol to leak data that can be used to recover the site's private key using what's known as a side-channel attack.
As a result, someone monitoring the connection between a visitor and site who happens to witness the rarely occurring fault (or even the visitor themselves) can cryptographically impersonate the website. Most developers heeded Lenstra's call to introduce countermeasures that check for the signature faults and prevent them from spilling the sensitive mathematical data, but a variety of HTTPS software—including GNUTLS, PolarSSL, and libgcrypt—by default contain no such hardening. And even when software implements the checks by default, certain types of configurations can turn them off.
"This report shows that it is still possible to use Lenstra's attack to recover RSA private keys, almost two decades after the attack has been described first, and that fault-based side-channel attacks can be relevant even in scenarios where the attacker does not have physical access to the device," Red Hat's Weimer wrote in this week's paper. "The net effect is that a passive observer with visibility into global Internet traffic is likely able to recover quite a few RSA keys in a completely non-attributable fashion."
Much like the odds of winning a lottery, the chances of witnessing an RSA signature fault are astonishingly small, and there's no way an attacker can produce key leaks for a given site at will. Still, Weimer's nine-month experiment demonstrates that patient adversaries who are interested in impersonating a wide range of sites will eventually succeed, and success will only grow with time and with the number of simultaneous scans that are carried out. The obvious beneficiary of this technique would be the National Security Agency and other state-sponsored spy groups that are in a position to monitor huge amounts of Internet traffic.
Perfect in name only
Some of the devices Weimer observed leaking data were extremely old and were possibly in the process of failing. Others, including those from Hillstone Networks and ZyXEL, used a buggy version of the OpenSSL code library from third-party hardware provider Cavium. The vulnerability itself—CVE-2015-5738—was recently patched in Cavium's library. Weimer has a much fuller discussion of available fixes on page eight of his paper.
This week's findings come as more and more websites, chat applications, and other Internet services are implementing perfect forward secrecy. The key-agreement protocol makes it possible for parties to use ephemeral keys that change regularly. The rotating key scheme makes spies work much harder to decrypt communications and prevents a successful attack on one encrypted session from revealing the contents of earlier or later sessions. Despite its name, though, perfect forward secrecy comes with its own weaknesses, which users must actively monitor.
Weimer said effective short-term fixes include the kinds of signature checks found in the NSS or OpenSSL code libraries. Still, those measures aren't always ideal. Over the longer term, the researcher said that TLS should possibly switch to a non-deterministic signature scheme. The changes are important, Weimer said. "However, none of these measures will help those operators who have been using unchecked RSA-CRT implementations for years and are now wondering if their RSA private keys have already leaked," Weimer wrote. Those affected should implement the short-term fix and regenerate their keys as soon as possible.
reader comments
21